23andMe resets user passwords after genetic data posted online
Days after user personal surfaced online, the genetic testing company 23andMe said it’s requiring all users to reset their passwords “out of caution.”
On Friday, 23andMe confirmed that hackers had obtained some users’ data, but stopped short of calling the incident a data breach. The company said that the hackers had accessed “certain accounts” of 23andMe users who used passwords that were not unique to the service — a common technique where hackers try to break into victim’s accounts using passwords that have already been made public in previous data breaches.
23andMe’s announcement came two days after hackers advertised an alleged sample of 23andMe user data on the hacking forum BreachForums, offering to sell individual profiles for between $1 to $10. The sample, which TechCrunch has seen, contained the alleged user data of one million users of Jewish Ashkenazi descent. Another user on BreachForums claimed to have the 23andMe data of 100,000 Chinese users.
Contact Us
Do you have more information about the 23andMe incident? We’d love to hear from you. You can contact Lorenzo Franceschi-Bicchierai securely on Signal at +1 917 257 1382, or via Telegram, Keybase, and Wire @lorenzofb, or email lorenzo@techcrunch.com. You can also contact TechCrunch via SecureDrop.
According to 23andMe, the data was “compiled” from users that had opted in to the DNA Relatives feature, which allows users who choose to switch on the feature to automatically share their data to others. In theory, this would allow a hacker to get more than one victim’s data just by breaking into the account of someone who opted into the feature.
Late on Monday, 23andMe published an update on its website, announcing that they forced all users to change their passwords, and saying they are “encouraging the use of multi-factor authentication.”
A 23andMe user, who asked to remain anonymous to protect their privacy, shared the email they received from the company, where 23andMe wrote that the company does “not have any indication at this time that there as been a data security incident within our systems, or that 23andMe was the source of the account credentials used in these attacks.”
The user told TechCrunch that they were a 23andMe beta tester since 2012, and they have watched their database and connections grow, “finding more cousins and even hidden siblings of parents.” And while 23andMe is “a cool product,” the user said, the company “knows a lot” and this is a “sad” incident.
It’s unclear if, as of this writing, all users have received an email prompting them to reset their passwords.
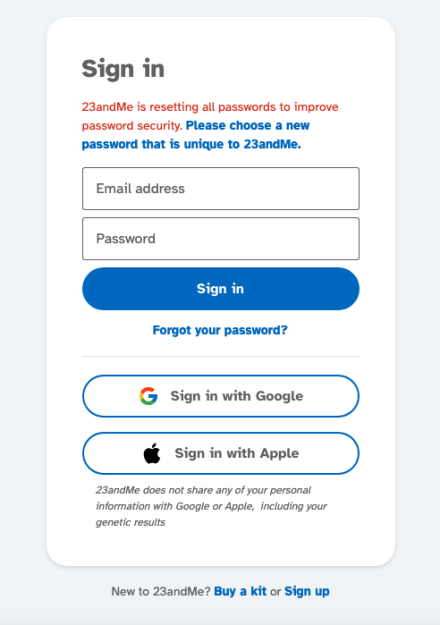
Another 23andMe user told TechCrunch that they haven’t yet received a password reset email. Instead, they said that when they tried to login, they saw a new message: “23andMe is resetting all passwords to improve password security. Please choose a new password that is unique to 23andMe.”
“I wasn’t able to login so I clicked ‘Forgot your password’ to update and re-login to my account,” said the user, who also asked to remain anonymous to protect their privacy.
The user shared a screenshot of the login page they saw:
23andMe did not answer to a series of questions, including whether it has verified that the leaked data is legitimate, whether it has revoked all users’ session tokens — meaning 23andMe logged out users on every device they were logged in — and whether the company changed its password policy. Instead, company spokesperson Andy Kill pointed us to the blog post, saying they will keep updating that.
Given that the alleged hacked data surfaced on Wednesday, and 23andMe only asked users to reset passwords five days later, a cybersecurity expert said the company could have been quicker in responding to the incident.
“I would like to see organizations proactively support their users in avoiding credential stuffing risk — and in the case of 23andMe, the reaction to force password resets could have happened much earlier, as soon as the credential stuffing attack was known,” Rachel Tobac, a hacker and CEO of SocialProof Security, told TechCrunch. “Eventually I would like organizations to focus on proactive rather than reactive actions to reduce this risk — and reactive responses need to happen quickly.”


