Quantum threats loom in Gartner’s 2023 Hype Cycle for data security
Head over to our on-demand library to view sessions from VB Transform 2023. Register Here
The best-run organizations prioritize cybersecurity spending as a business decision first, and Gartner’s Hype Cycle for Data Security 2023 reflects the increasing dominance of this approach. Key technologies needed for assessing and quantifying cloud risk are maturing, and new technologies to protect against emerging threats are predicted to gain traction.
Business cases are driving data security integration and technology
Gartner sees the core technologies needed to validate and quantify cyber-risk maturing quickly as more organizations focus on measuring their cybersecurity investments’ impact. CISOs tell VentureBeat that it is a new era of financial accountability, and that extends to new technologies for securing data stored in multicloud tech stacks and across networks globally. Getting control of cybersecurity costs is becoming a much higher priority as boards of directors look at how data security spending protects, and potentially grows, revenue.
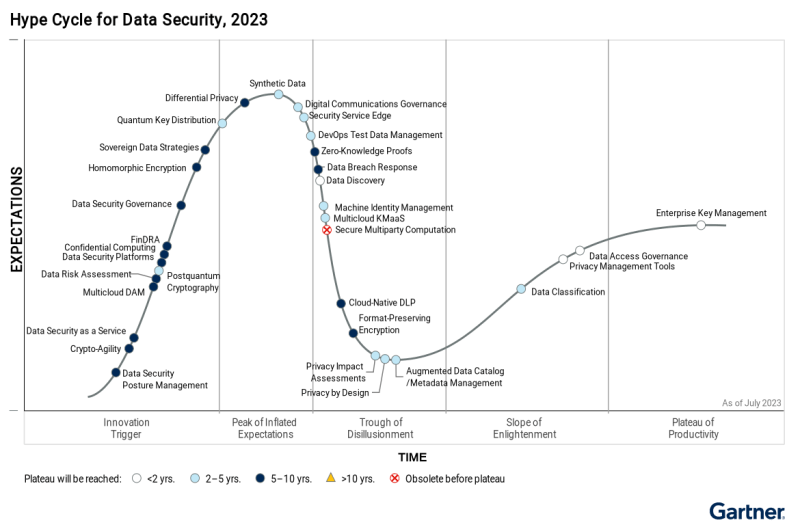
Gartner’s latest Hype Cycle for data security dovetails with what CISOs, CIOs and their teams tell VentureBeat, especially in compliance-centric industries such as insurance, financial services, institutional banking and securities investments. Gartner added five new technologies this year: crypto-agility, post-quantum cryptography, quantum key distribution, sovereign data strategies and digital communications governance. Eight technologies have been removed or reassigned this year.
Getting integration right in data security at the enterprise level has always been a challenge. The need for more secure approaches to data integration has led to a proliferation of solutions over the years, some more secure than others. Gartner predicts these challenges will shift or consolidate data security technologies, including data security posture management (DSPM), data security platforms (DSPs) and multicloud database activity monitoring (DAM).
Event
VB Transform 2023 On-Demand
Did you miss a session from VB Transform 2023? Register to access the on-demand library for all of our featured sessions.
CISOs also say they are monitoring quantum computing as an evolving potential threat and have delegated monitoring it to their strategic IT planning teams. Gartner also introduced crypto-agility in this year’s Hype Cycle, responding to its clients’ requests for as much data and knowledge as possible in this area.
2023 key trends in data security
CISOs and the teams they manage tell VentureBeat that protecting data in the cloud, and the many identities associated with each data source across multicloud configurations, is getting more challenging given the need to provide access rights by data type while still tracking compliance.
That’s made even more difficult by the exponential growth of machine identities across enterprises’ cloud instances. This year’s Hype Cycle for data security underscores this and other trends summarized here.
Data governance and risk management are now strategic priorities
Board members regularly question CISOs about governance and risk management. CISOs tell VentureBeat that while board members know risk management at an expert level, they need to have the technology-based context of data governance and risk management defined from a tech stack and multicloud perspective.
These dynamics between boards and CISOs are playing out across hundreds of companies as data governance and risk management dominate Gartner’s discussions in this year’s Hype Cycle. Boards want to know how to accurately quantify cyber-risk, which drives greater compliance. CISOs say that financial data risk assessment (FinDRA) is board-driven and weren’t surprised it appears on the Hype Cycle.
Moving data to the cloud increases the need for data-in-use protection technologies
Nearly every business relies on cloud services for a portion, if not all, of their infrastructure and application suites. Gartner sees this as a potential risk for data and has identified a series of technologies and techniques on the Hype Cycle to protect data in use and at rest.
These include confidentiality, homomorphic encryption, differential privacy and secure multiparty computation (SMPC). Confidentiality relies on hardware-based trusted execution environments to isolate data processing, while SMPC allows collaborative data analysis without exposing raw data. The presence of these data-in-use technologies on the Hype Cycle demonstrate the shift from data security at rest to data security in transit.
New quantum computing-based threats on the horizon
Much has been written and predicted about when quantum computing will break encryption. In reality, no one knows when it will happen; however, there’s wide consensus that quantum technologies are progressing in that direction. CISOs VentureBeat interviewed on the topic see cryptography at varying levels of urgency depending on their business models, industries and how reliant they are on legacy encryption.
Gartner added both crypto-agility and post-quantum cryptography to the Hype Cycle for the first time this year. CISOs are pragmatic about technologies with as long a runway as these have. In previous interviews, CISOs told VentureBeat they could see where post-quantum cryptography could strengthen zero-trust frameworks in the long term.
New technologies added to the hype cycle
Together, Gartner’s five new hype cycle technologies prepare CISOs for the next generation of quantum threats while addressing the most challenging aspects of governance and data sovereignty. The five newly added technologies are briefly summarized here:
Crypto-agility
The purpose of crypto-agility is to upgrade encryption algorithms used in applications and systems in real time, alleviating the risk of a quantum-based breach. Gartner writes that this will enable organizations to replace vulnerable algorithms with new post-quantum cryptography to ward off attacks using quantum computing to defeat encryption. Crypto-agility offers CISOs a path to secure encryption as quantum capabilities advance over the next five to seven years.
Post-quantum cryptography
Gartner defines this new technology as based on new quantum-safe algorithms, such as lattice cryptography, that are resistant to decryption by quantum computers. The use case Gartner discusses in the Hype Cycle centers on using this technology in a pre-emptive strategy against quantum-based threats.
VentureBeat’s interviews with CISOs at financial trading firms revealed that pro-forma tech stacks already defend against quantum computing risks and threats. Gartner’s latest addition will likely be added to roadmaps for further evaluation by those CISOs responsible for commercial banking and other financial services and institutions. Leading vendors include Amazon, IBM and Microsoft.
Quantum key distribution (QKD)
This technology works by using quantum physics principles, including photon entanglement, to create and exchange tamper-evident keys. Gartner considers QKD a niche technology today. But given its nature, uses in applications critical to national security are a natural extension of its strengths, as it’s anticipated to be useful for exchanging high-value data. Leading vendors include ID Quantique, MagiQ Technologies and Toshiba.
Sovereign data strategies
This is a new addition to the Hype Cycle that supports data security governance, privacy impact assessment, financial data risk assessment (FinDRA) and data risk assessment. Sovereign data strategies reflect efforts by governments to provide strong governance and data security for their citizens and economy.
Privacy, security, access, use, retention, sharing regulations, processing and persistence are examples cited by Gartner. According to the firm, sovereign data strategies will eventually become table stakes for any business that needs to complete transactions across sovereign jurisdictions.
Digital communications governance
Digital communications governance (DCG) solutions monitor, analyze and enforce employee messaging, voice and video compliance policies. DCG platforms also manage regulatory and corporate governance requirements with data retention, surveillance, behavioral analytics and e-discovery. They help compliance teams identify misconduct and comply with regulations by monitoring communications data.
DCG also helps CIOs and CISOs manage employee messaging, voice and video platform risks by consolidating access and enforcement across communication channels. Leading vendors include Global Relay, Proofpoint and Veritas.
Trends most strongly driving the future of data security
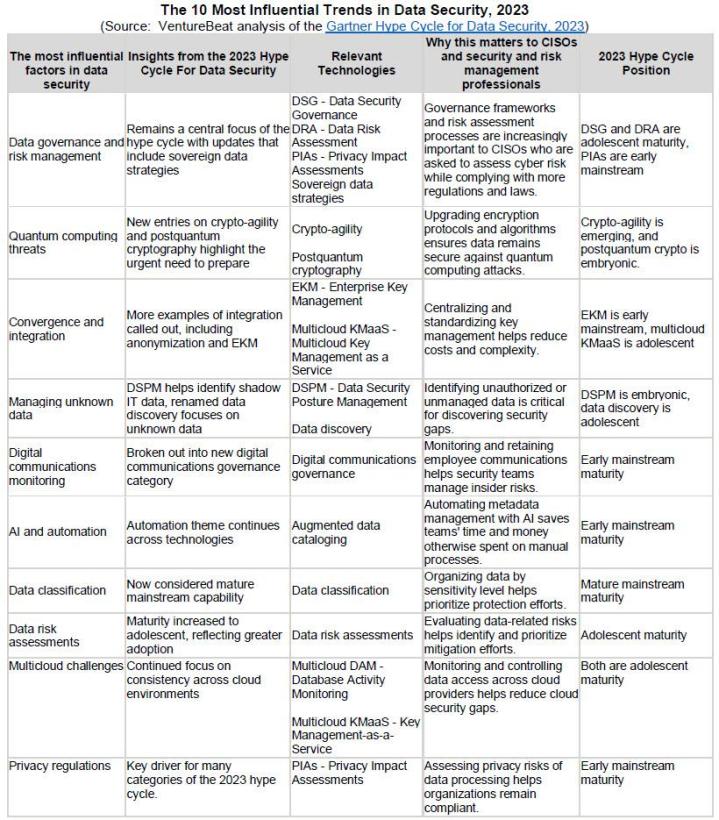
Ten key trends emerge from this year’s Hype Cycle. Data governance, risk management and compliance are core drivers of the data security market. Gartner believes that preparing for quantum computing threats, convergence and integration of security tools, and managing unknown shadow IT data are high priorities.
The following matrix compares the most influential factors, in order of priority, that are influencing the future of data security.
VentureBeat’s mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Discover our Briefings.


